How To Register Fortinet Device
KB ID 0001725
Trouble
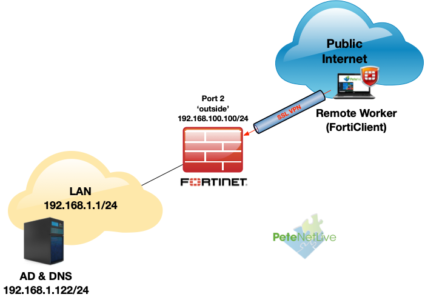
FortiGate Remote Access (SSL–VPN ) is a solution that is a lot easier to setup than on other firewall competitors. Here'southward how to setup remote access to a FortiGate firewall device, using the FortiClient software, and Agile Directory authentication. This is what my topology looks similar;
Note: I've inverse the FortiGates default management HTTPS port from 443 to 4433 (earlier I started). This was to permit me use the proper HTTPS port of 443 for remote admission SSL VPN. I propose you too practise this, equally running SSL-VPN over an 'odd' port may not work from some locations. Run into the following article;
FortiGate: Alter the HTTPS Management Port
Document: I'k also using a self signed certificate on the FortiGate, in a production environment you may want to buy a publicly signed one!
Step 1: FortiGate LDAPS Prerequisites
Earlier we first, we demand to make sure your firewall tin resolve internal DNS. (Because the Kerberos Document name on your Domain Controller(south) gets checked, when doing LDAPS queries, if you DON'T desire to do this then disable server identity check when you lot setup your LDAP server below). Or you can add the IP address to the servers Kerberos certificate every bit a ' Subject Culling Name ' but thats a bit bobbins IMHO
Network > DNS > Specify > Add in your 'Internal" DNS servers > Apply.
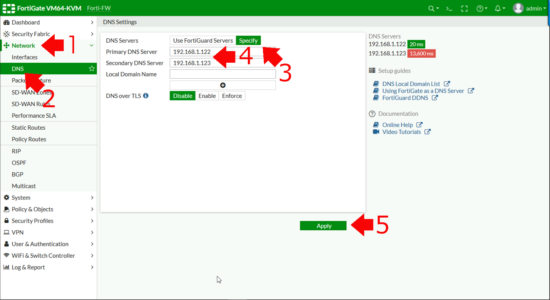
Document Prerequisites
To perform LDAPS the FortiGate needs to trust the certificate(s) that our domain controller(south) use. To enable that you need a re-create of the CA Certificate, for the CA that issued them. At this betoken if you're confused, you might want to run through the following article;
Get Set for LDAPS Channel Bounden
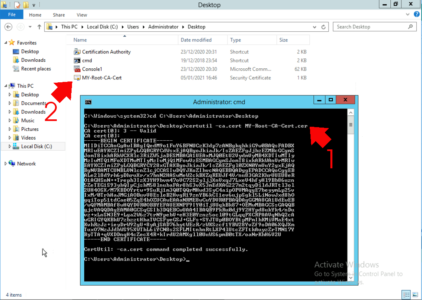
So to get a copy of your CA cert on a Windows CA server utilize the following command;
certutil -ca.cert My-Root-CA-Cert.cer
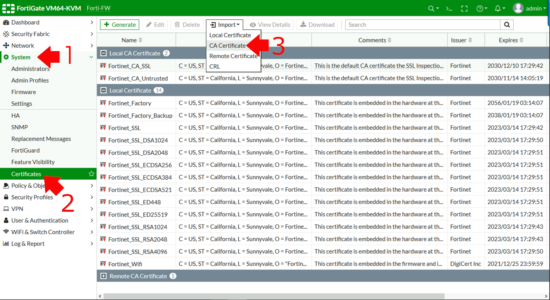
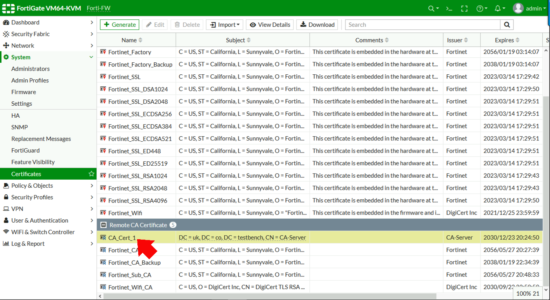
To ' Import ' the document into the Fortigate > System > Certificates > Import > CA Certificate.
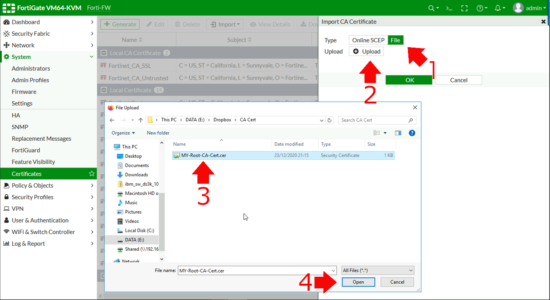
File > Upload > Scan to your CA Document > Open > OK.
Take annotation of the certificate name, (CA_Cert_1 in the example below,) y'all will need this data below.
Step two: Permit FortiGate LDAPS Authentication (Active Directory)
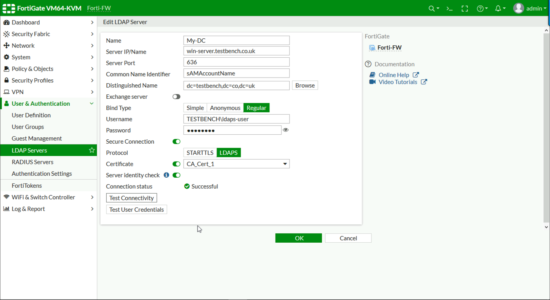
User & Authentication > LDAP Servers > Add together.

- Name: Something Sensible!
- Server IP/Proper noun: Employ the FQDN of the server (or you demand to put the IP on the Kerberos document every bit a SAN!)
- ServerPort: 636 (Nosotros're not using 389 LDAP is Not secure!)
- Common Name Identifier: sAMAccountName
- Distinguished Proper noun: Enter the DN for either the top level of your domain or an OU that'due south got all your users/groups in.
- Bind Type: Regular.
- Username: in DOMAIN\username format Note: A normal domain user account is sufficient it DOES NOT need to be a domain ambassador.
- Countersign: For the above user.
- Secure Connection: LDAPS.
- Document: Select YOUR CA Document.
- Server Identity Check: Enabled.
Click ' Test Connectivity ' It should say successful, and so you can check some other domain user credentials as a exam > OK.
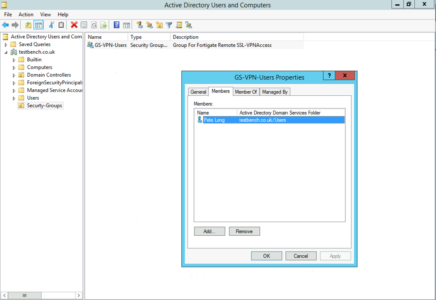
Domain / Active Directory Setup
Over in my Active Directory I've created a security grouping called GS-VPN-Users, and put my user object into it.
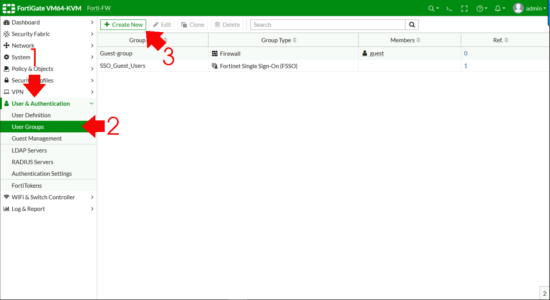
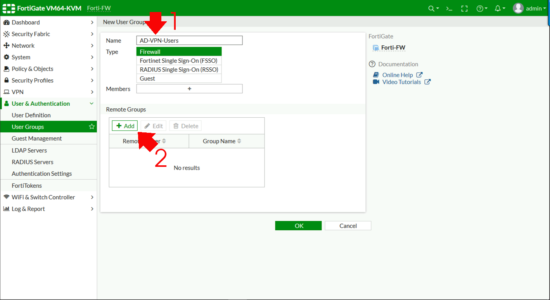
At present I need to create a FIREWALL GROUP and add my ACTIVE DIRECTORY Group to that. User & Authentication > User Groups > Create New.
- Name: Something sensible!
- Type: Firewall
Remote Groups > Add.
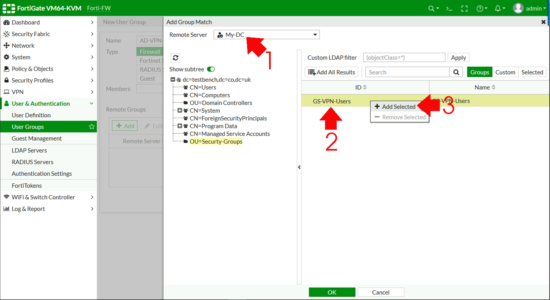
Change the Remote Server drop downwards list to exist your LDAPS Server > Browse to your Active DIRECTORY GROUP, right click and Add together Selected (Cheers, that took me three goes to find FortiNet!) > OK.
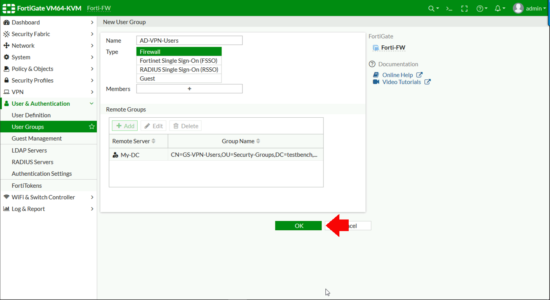
All existence well you lot should see your LDAPS server AND the distinguished name of your AD grouping, (check that's non missing!) > OK.
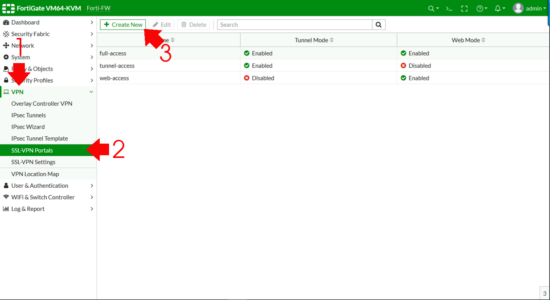
Step iii: Setup FortiGate SSL-VPN
First we need an SSL Portal > VPN > SSL-VPN Portals > Create New.
- Name: Something sensible!
- Enable Divide Tunnelling: Enabled. (If you don't do this then remote clients need to come though the FortiGate for spider web admission, I usually enable split tunnel).
- Source IP Pools: Add together And then Create.
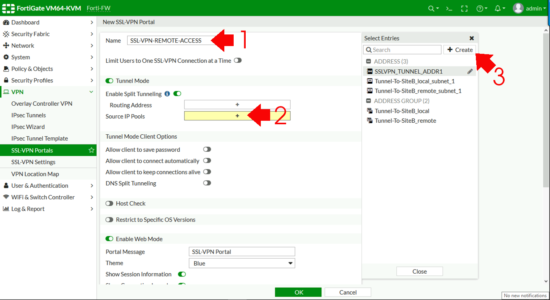
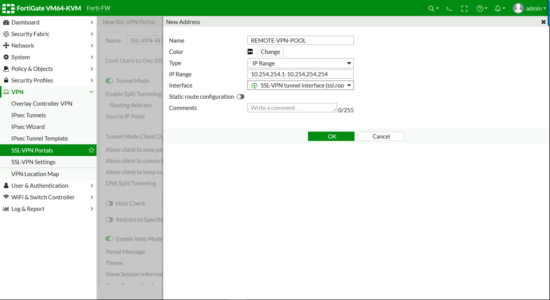
Address.

- Proper name: Something sensible!
- Blazon: IP Range
- IP Range: The subnet you want to apply. (Note:If you are routing on your LAN, brand sure there'south a route back to the FortiGate for this subnet or bad things will happen!)
- Interface: SSL-VPN tunnel interface
OK.
Enter a portal bulletin, (the header on the folio once a remote user connects) > Enable FortiClient download > OK.
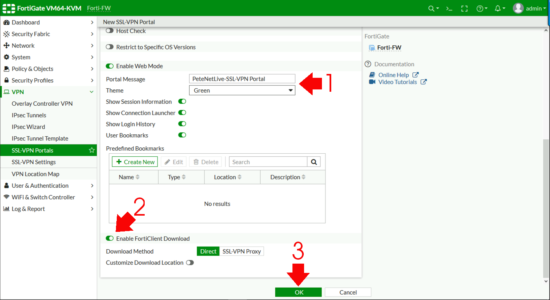
If you see the following error, that'south because on some smaller firewalls, (like the 40F) there can only be 1, so you demand to edit the one that is there past default.
Maximum number 0f entries has been reached.
FortiGate SSL-VPN Settings
VPN > SSL-VPN Settings > Mind on Interfaces.
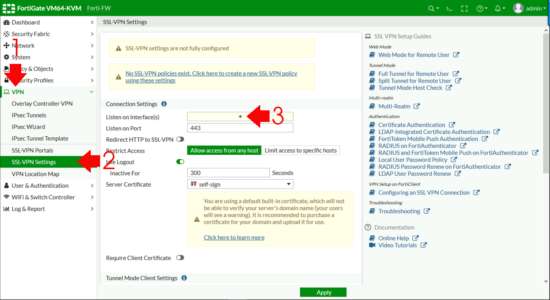
Set to the outside (WAN) interface > Address Range > Specify custom IP Ranges > IP Ranges > Add in the pool y'all created above.
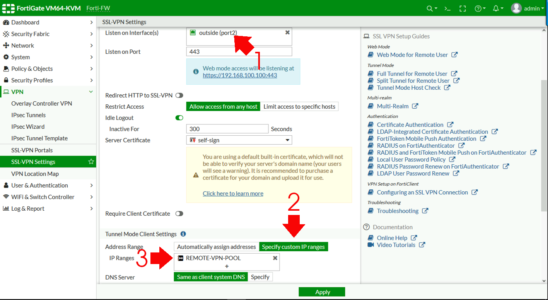
DNS Server > Specify > Add in your internal DNS servers > Authentication Portal Mapping > Create New.
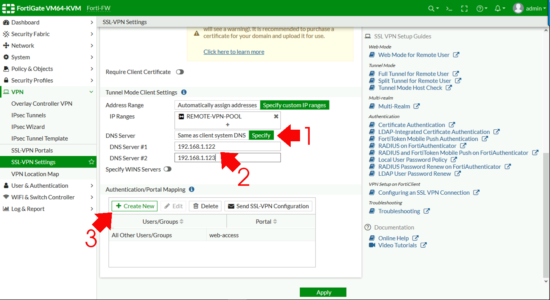
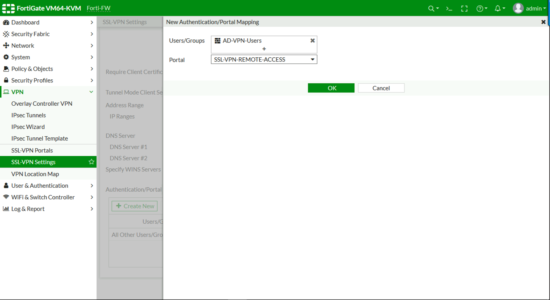
- Users/Groups: Your FIREWALL Group.
- Portal: Your Portal
OK.
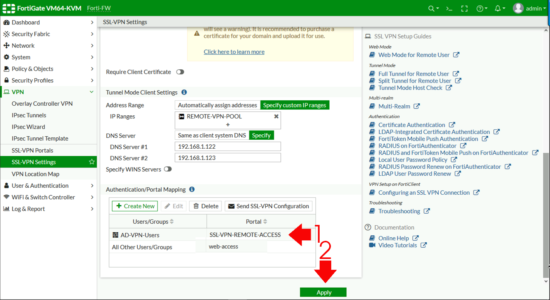
Apply (Note: If it complains ' All Other User/Group ' is non configured, set that to web-access (as shown).
FortiGate SSL-VPN Firewall Policy
Policy & Objects > Firewall Policy (or IPV4 Policy on older versions) > Create New.
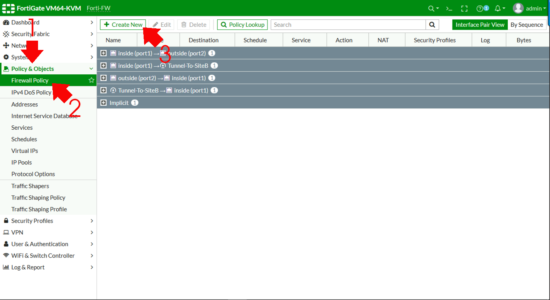
- Name: Something sensible.
- Incoming Interface: SSL-VPN Tunnel Interface.
- Outgoing Interface: Within (LAN).
- Source: Your remote IP Pool AND your FIREWALL GOUP.
- Destination: Local LAN (remember if you want DMZ access, add together that in also)
- Schedule: Always
- Action: Accept
- NAT: Disabled
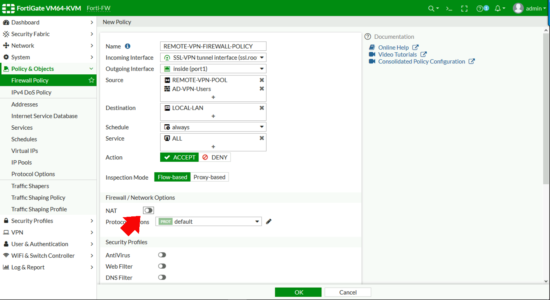
- Generate logs when session starts: Enabled
OK.
Pace 4: Test FortiGate SSL-VPN
From your remote customer, browse to the public IP/FQDN of the firewall and log in, you should see the SSL-VPN portal you created, and take the option to download the FortiClient (VPN) software for your OS version.
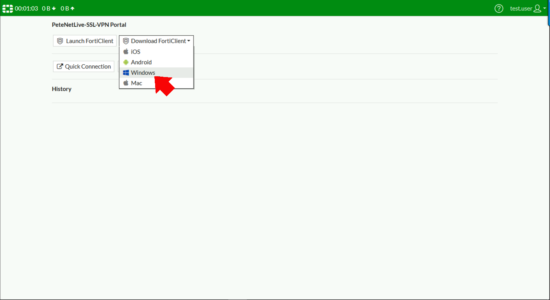
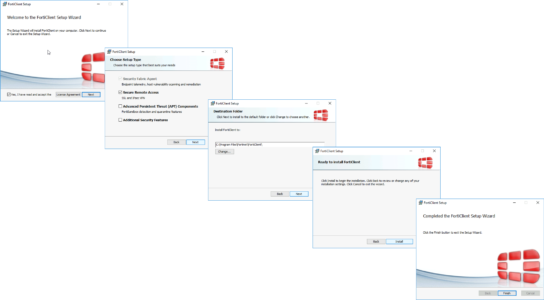
Install the FortiClient (Note: This is but the VPN component not the full FortiClient).
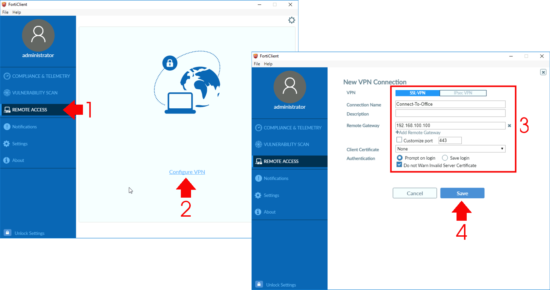
Remote Admission > Configure VPN.
- VPN: SSL-VPN.
- Connection Proper name: Something sensible.
- Remote Gateway: IP or FQDN of the FortiGate.
- Hallmark: Prompt on Logon (unless you desire information technology to retrieve).
- Do not warn invalid Server Document: Enabled (Unless y'all are using a publicly signed certificate on your FortiGate).
Save.
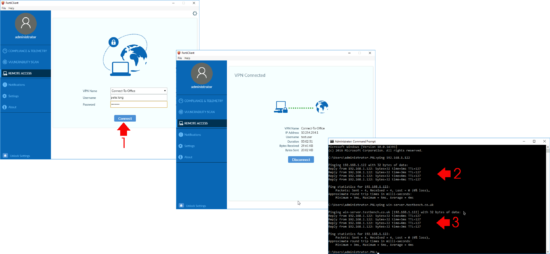
Then test connection, make certain you can ping internal IP addresses and DNS names.
Related Articles, References, Credits, or External Links
NA
Source: https://www.petenetlive.com/kb/article/0001725
Posted by: catronacloned.blogspot.com


0 Response to "How To Register Fortinet Device"
Post a Comment